Introduction
What is SQL Injection?
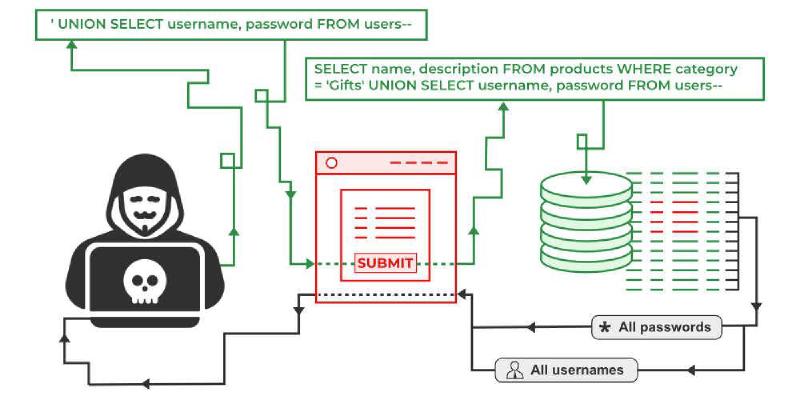
SQL injection (SQLi) is a security vulnerability that allows an attacker to execute SQL Statements on the target server. It may allow an attacker to retrieve your data, bypass your login mechanism, delete your database and even get the system shell.
The reason for this vulnerability is that some developers directly use user input to do SQL queries, such as checking if the input username and password correspond to those in the database. This gives the attacker a chance to inject SQL statements in the input and the system will execute those Trojan SQL statements.
Here is an example:
The server SQL query may be like: SELECT * FROM users WHERE user='$user' AND passwd='$passwd'
If my user input is admin' and '1=1'; -- //
Then the final SQL statement will be like: SELECT * FROM users WHERE user='admin' and '1=1'; -- //' AND passwd='$passwd'
In this way, we can successfully login with user ‘admin’.
Injection Method
There are many ways to make a SQL Injection. Sometimes, even if the SQL statement which we inject has been successfully executed, the server will not give us direct feedback, this makes it difficult for us to obtain the information. At this time we can use other methods to get the information we want. Here are some common methods which we can use to do the SQL Injection.
- UNION-based: This is the most direct way. Suitable for the web page will directly display the SQL query result. In this way we can use UNION statement to query other data in the database. The web page will display the information that we want to query with the information normal.
- Error-based: Suitable for when an SQL statement error occurs, the web page will display the error message. We can put a Trojan SQL statement in a wrong SQL statement, so that the system will execute the Trojan statement first and feed back the query results of the Trojan SQL statement to us through the error message generated by the incorrect SQL statement.
- Time-based blind injection: Suitable for the web page don’t display any message, we can use specific time delay function (For example in MSSQL: WAITFOR DELAY ’0:0:5′) to determine whether the SQL statement is successfully injected.
- Boolean-based blind injection: This is the most complicated way. Suitable for the server that only return if the result of the SQL statement is true or false. We can use a script to guess the ASCII code of each letter of the query result through enumeration. For example, we can use
ascii(substr(database(),1,1))>nto determine whether the ASCII code of the letter 1 of the database name (query by executedatabase()) is greater than n. If the guess is correct, the system will return true, and if the guess is wrong, it will return false. In this way, we can obtain the database information little by little.
SQLmap
sqlmap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. Here I will teach you some common arguments of sqlmap:
- -u [URL]: Specify your target URL
- -p [keyword]: indicate variable used to pass SQL commands. Example:
sqlmap -u http://192.168.0.1/login.php?user=1 -p user - –dump: To dump the entire database, including user credentials.
- -r [file]: post request file
- –os-shell: provides us with a full interactive shell.
- –dbs: list all database
- –tables: list all tables
- –columns: list all columns
- –data=[post request]
- –method=[GET/POST]
By the way
SQLmap is a very powerful tool for automating SQL injection, but while we are able to use the tool, we should also know how to do SQL injection manually, we need to understand how it works. If you need more example, you can find some SQLi Cheat Sheet, like this. Hope these contents can help you. And finally, I hope you won’t just be a script kiddie :)